Trusted By Customers Worldwide










BreezN visitor management software has been rebranded to SV3 Enterprise®
Building Intelligence, providers of SV3®, the patented SafetyAct Certified technology for visitor, vehicle, and vendor management have rebranded BreezN to SV3 Enterprise® to provide additional features and benefits to its users.
SV3 Enterprise® Visitor Management
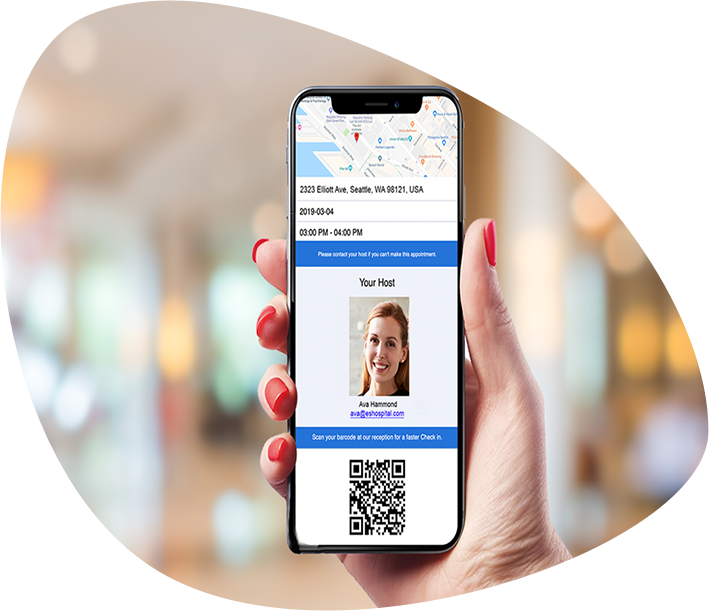
Visitor Check-In Process

01. Pre-Registration
Visitors receive an email with meeting details and a QR code to check-in with.

02. Seamless Arrival
Upon arrival, the visitor scans their QR code or signs in manually at the iPad kiosk.

03. Host Notification
The host receives an instant notification via email or text after their visitor has checked-in.



Manage your visitors with ease
- Faster check-ins: schedule your visitors for quick check-in with automated emails and QR codes.
- Lobby kiosks: secure unmanned entrances with kiosks, cutting down security threats and unwanted traffic.
- Background checks: instantly run background checks on visitors as soon as they check-in.
- Watch lists and alerts: screen against internal and external watch and barred visitor lists, and receive automatic security alerts for barred visitors.
- Multiple locations: increase workplace security with full transparency of visitors across all locations at any time.
- Real-time reports: view current visitors, activity, alerts, and run reports in real-time — instantly improving security and workflows for your business.
Cloud-based, private environment offers the ultimate data protection
New data security standards
Dedicated Environment
Your data will be stored on its own Microsoft Azure environment, not on a shared server with other organizations’ data—reducing the risk of cyber attacks.
Data Encryption
Customer data is secure at all phases of its lifecycle: 256-bit AES encryption while at rest. TLS 1.2 encryption in transit.
Data Centers
Data centers undergo third-party audits to review security, availability, integrity and confidentiality. Azure data centers are SOC 1 (SSAE 16), Type II, and SOC 3 certified.
Secure Data Flow
We protect our systems from malware, distributed denial-of-service (DDoS) attacks, and other threats with the latest Microsoft technologies.

Compliance requirements shouldn’t be a burden for your organization
Compliance Regulations and Visitor Management
C-TPAT
C-TPAT holds importers responsible for implementing best practices for security across their supply chain to avoid running into any problems when products arrive at the border. Our solution features ID scanning and photo badge printing capabilities to identify unauthorized/unidentified persons efficiently.
GDPR
GDPR affects the way that data is stored across every industry, from pharmaceutical services to manufacturing companies and more. BreezN’s data management system allows for secure and reliable data processing, management, and encryption that meets the mark of GDPR.
HIPAA
Companies that deal with protected health information (PHI) must have physical, network, and process security measures in place and follow them to ensure HIPAA compliance. Our software allows for the screening of visitors against internal and/or government-issued watchlists, as well as security alerts if an unauthorized visitor attempts to access your facility.
OSHA
Record-keeping is imperative in meeting the standards of OSHA, as is the level of worker accessibility to these records. Having a digital check-in system that provides real-time visitor details allows you to run reporting at a moment’s notice.
SOC 2
Companies who store data in the cloud must abide by a set of policies. These policies monitor the security, availability, processing integrity, confidentiality, and privacy of customer data. Our software is hosted on the Microsoft Azure Cloud which offers SOC 1, 2, and 3 reports.
JCAHO
JCAHO compliance requires healthcare facilities to be able to communicate with and evacuate visitors. The Joint Commission has standards on confidentiality and security similar to those of HIPAA.
FSMA
For companies to comply with FSMA the FDA compiled a database of mitigation strategies, and one of the strategies is to implement a check in/check out procedure at security or reception areas, which includes verification of proper identification and screening equipment.
ITAR
ITAR requires documentation that includes licenses, shipping documents for goods, in addition to citizenship verification, technology control plans, and nondisclosure agreements for all visitors to your facility.
GLBA
Our software helps companies meet and maintain GLBA compliance around physical security by assisting with verifying visitor identity and denying access to those who are not permitted, maintaining digital visitor logs, and creating badges that identify visitors.
Trusted by Fortune 100 for the last decade
Learn why companies around the world have chosen SV3 Enterprise® to improve security, operations, and visitor experience.
Security, compliance, and convenience at every stage.
Manage reopening and visitor check-in more effectively.